CBA Website Archive (Until 2023)
Contact Webmaster
LISP Packet Dissector
This page is the home of an effort to develop a complete dissector plugin for the Locator/ID Separation Protocol (LISP) within the Wireshark network analyzer. Work started against the 1.2.x branch of Wireshark, followed by the 1.4.x branch, with version 20110422 of the patch being accepted for inclusion into the 1.6.x branch. A second upstream submission was version 20120819, which is now part of the 1.9.x development branch, and will be released in the 1.10.x stable series.
Update (2013/06/27): LISP packet dissector is a project currently maintained by Lorand Jakab. On May 2013, Radu Terciu contributed to Lorand's code extending LCAF support with the types defined up to date. At the time of this writing, LCAF defines 13 different types. All of them are currently supported on the Wireshark LISP dissector thanks to Radu's contribution.
Development of the dissector is still active after upstream inclusion, with new features and bugfixes showing up on this page first. If you are not interested in features that were added after version 20110422, just grab the latest stable source or binary package directly from the official Wireshark download page (or if your OS has package management, use the included package, as long as it's version 1.6.0 or higher). If you want the features and fixes added between versions 20110422 and 20120819, you still have the option of not compiling from source on Windows and on the Mac, by using the official automated builds. And if you want the latest and greatest, follow the steps below, and keep checking back to this page. See contact info at the bottom of the page if you want to receive updates.
Packet dissection is based on draft-ietf-lisp-23, draft-farinacci-lisp-lcaf-10, and draft-ermagan-lisp-nat-traversal-01.
Source Code
The dissector used to be released as a patch against mainline. Version 20120819 was the last in patch form, from now on there will be no more point releases. Rather, you will be able to download the latest version of the packet-lisp.c file, which implements the LISP control packet dissector. Since the upstream inclusion no Makefiles need to be modified, all you need to do is overwrite this file, making patching unnecessary.
Step-by-step instructions:
- Download the latest stable source tarball from the Wireshark download page.
- Download the latest revision of the dissector code.
- Extract the Wireshark source.
- Overwrite
epan/dissectors/packet-lisp.cwith the file downloaded in step 2. - Build from source as you normally would. Note that you can personalize how Wireshark is compiled on your system, see
./configure --helpfor an extensive list of options. Refer to the Wireshark documentation for more help on how to build from source. - (Optional) Check revision history, to know what's new.
The above steps should translate roughly to the following commands:
wget http://www.wireshark.org/download/src/wireshark-1.8.x.tar.bz2
wget http://raw.github.com/ljakab/lisp-dissector/master/packet-lisp.c
tar xvf wireshark-1.8.x.tar.bz2
cp packet-lisp.c wireshark-1.8.x/epan/dissectors
cd wireshark-1.8.x
./configure --help
./configure
nice make -j4
sudo make install
Caveats
You should be aware that capturing on the same machine that generates the packets you are interested in may cause issues with checksums, due to hardware offloading to the NIC. For example, if you use a Linux host to generate Map-Request messages, and capture those packets with Wireshark on the same host, UDP checksums may be shown as incorrect (except if you used raw UDP sockets to generate them). You may solve this by disabling checksum offloading on your NIC, if this operation is supported. Using ethtool, you can check for offload status:
ethtool --show-offload eth0
If transmit checksum is on, you can disable it by running:
ethtool --offload eth0 tx off
For more information, see the Wireshark wiki on this topic.
Version history (discontinued)
- 20120819
- Feature: support for the following LCAF types: AFI List, Instance ID, Explicit Locator Path (ELP); see draft-farinacci-lisp-lcaf-10 for details
- Minor bug fixes
- 20120315
- Feature: support for new NAT traversal specific control packets (Info-Request/Info-Reply) and changes to existing types, as defined in draft-ermagan-lisp-nat-traversal-00
- Some code cleanup
- Some small bug fixes
- 20110622
- Feature: show if a Map-Request is SMR, SMR-invoked, RLOC-Probe, or sent by a P-ITR in Info column
- Feature: show if a Map-Reply is an RLOC-Probe response in Info column
- 20110422
- Feature: Map-Notify support
- Feature: show EID prefix contained within control packet in Info column (idea by Jesper Skriver)
- 20110329
- Code cleanup in preparation of upstream submission
- Reserved bits are now shown everywhere
- Support for PITR and SMR-invoked bits in Map-Requests (-11)
- Map-Reply record at the end of Map-Request packets is now dissected when M bit is set
- Mapping version is now shown
- Action for mapping is now shown
- Bugfix: Local bit is interpreted for IPv6 locators as well
- Bugfix: Map-Register Proxy-Map-Reply flag is now correctly interpreted
- Branch 1.2.x unsupported
- 20101020
- Better handle locators and prefixes with unexpected AFIs in Map-Replies
- 20100812
- Fixed issue of previous version skipping the Source-EID-AFI field and incorrectly identifying ITR-RLOC 1 as being Source-RLOC
- Added display filter for Source-EID-AFI
- 20100725
- Updated for the new -07 control packet format
- Map-Request flags are now decoded
- Mapping records have their sub-tree with details, highlighting individual fields
- 20100504
- Initial version
Screenshots
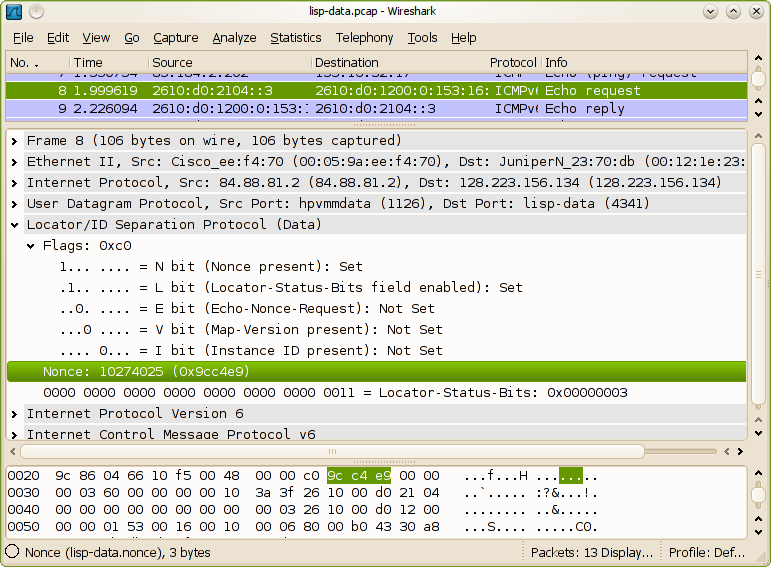
LISP encapsulated data packet
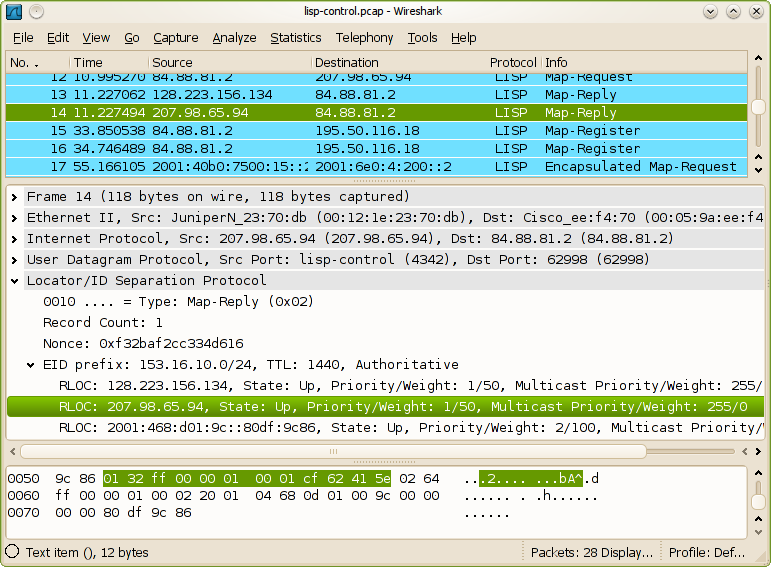
LISP control packet
Contact
For bug reports, constructive criticism, and contributing back improvements, or if you wish to be notified when a new version is available, please send email to Lori Jakab - This email address is being protected from spambots. You need JavaScript enabled to view it. . If you report a bug, please provide a capture file that reproduces it.
Important updates are announced on the author's Twitter and Identi.ca feeds. You can also find him hanging out in #lisp-networking and #lispmob on FreeNode (look for Lori).